Towards Post-quantum Cryptography
Published on March 3, 2025
🚀 Post-Quantum security: Why You Should Start Using SHA-3 for hashing
At Planisys - Cybersecurity, I’m exploring OpenSSL liboqs for post-quantum encryption to enhance DNS security and protect against future quantum threats. In parallel, I’ve been testing SHA-3 hashing with OpenSSL 3.0.x (Debian 12 package) as a practical step toward future-proofing DNS records, RPZ zones, and API communications.
We should start future-proofing our systems now. The quantum era isn’t far off, and Grover’s Algorithm effectively halves the number of brute-force quantum operations required to break hashed passwords. If you’re concerned about potential collisions or the reverse engineering of SHA-1 signatures in the future, it’s better to re-hash your data using SHA-3 for stronger quantum-resistant protection.
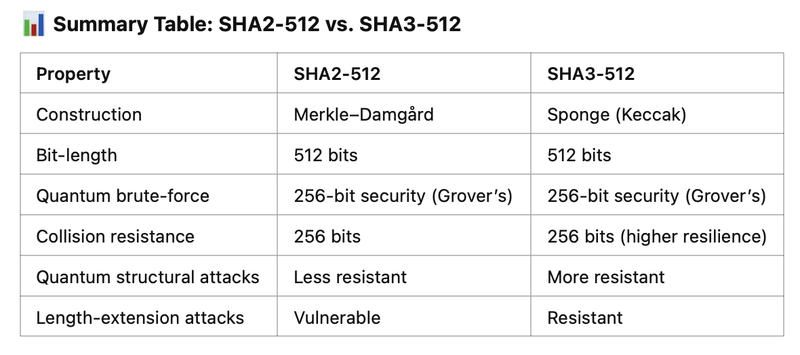
While Ethereum uses Keccak-256, it’s important to note that it’s not the same as SHA-3. SHA-3 was standardized by NIST, introducing critical changes like different padding rules for added security and domain separation.
🔒 Quantum Resistance & Cryptographic Strength
SHA-3 offers better quantum resistance compared to SHA-2 because they are based on fundamentally different cryptographic principles. This makes SHA-3 a better candidate for long-term data protection.
🔑 When to Use SHA-3 Instead of SHA-2
• 🔐 Data Integrity & Security: Use SHA-3 for hashing sensitive data, API tokens, or backup hashes where quantum resistance matters.
• 📧 Email Security: Future-proof your email systems by using SHA-3 for DKIM signatures.
• 🌐 DNS Security: Apply SHA-3 for DNSSEC signatures to enhance post-quantum security.
• 🐍 Python Applications: Replace SHA-2 with SHA-3 in applications where cryptographic strength is critical.
E.g. try this:import hashlib
data = b"Secure data that needs hashing"
hash_object = hashlib.sha3_512(data)
print(f"SHA3-512 Hash: {hash_object.hexdigest()}")
hashtag#openssl hashtag#sha3 hashtag#blockchain hashtag#ethereum hashtag#cryptography hashtag#quantumcomputing hashtag#cybersecurity hashtag#postquantumcryptography
